Macro-based malware strikes again: How to keep your networks safe

Image: Trend Micro
macromalwaretrendmicrofeb2015.jpg

Digital bad guys are once again pushing macro-based malware. After a 10-year hiatus, in January 2015 Microsoft Malware Protection Center reported a huge spike in two malicious macros: Adnel and Tarbir.
Trend Micro's Trend Labs also reported an uptick in macro-based malware, as the graph at the beginning of this article indicates. "Though we are mostly seeing UPATRE malware attached to spam, macro-based malware in spam has slowly been gaining traction since December 2014."
This is disturbing, as macro-based malware seemed to be out of the picture ever since Microsoft decided that Disable all macros with notification should be the default setting in Office products that use macros (Access, Excel, PowerPoint, Publisher, Visio, and Word).
Authentic phishing email
A possible reason macro-based malware is back and so successful is the quality of phishing letters used by the dark side; phishing campaigns are fooling more people than ever before. "Spam with macro-based malware typically make use of social engineering lures like remittance and invoice notifications, emails related to tax and payment slips, payment confirmation, purchase orders, etc.," mentions Maydalene Salvador, anti-spam research engineer at Trend Labs in this report. "Most of the spammed emails even contain so-called shipping codes in the email subject to appear authentic."
Whatever the bad guys are doing, it gets people to open the attachment. The attack falls apart if the person who opened the email realizes it is a scam and does not open the attachment.
If the user is fooled and opens the attached file, one of two things happens. The file will be unreadable and an alert will inform the user that macros need to be enabled, similar to the following example from Trend Labs. And being nice, the bad guys will often provide step-by-step instructions on how to enable macros.
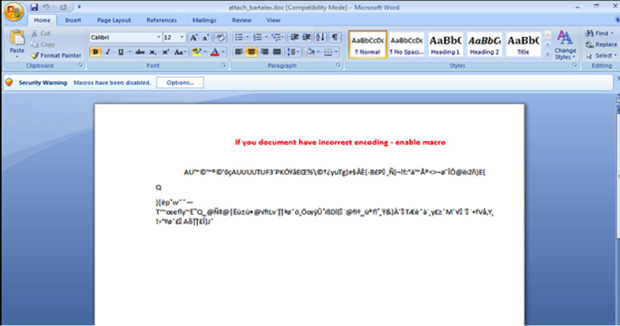
Image: Trend Micro
macromalwaretrendmicro.png

The second possibility is a window, similar to the official one below, will pop up. In this case the user, if agreeable, clicks Enable Content, and the macro malware will download onto the computer.

Image: Screenshot by Michael Kassner
macromalwarewarningkassnermarch2015.png

What are macro-based viruses, and why are they a problem?
Microsoft describes a macro as a series of commands or instructions grouped together as a single command to accomplish a task automatically. Bad guys latched onto that capability, and figured out how to write malware-laden macros that run as soon as the file is opened; the person who opens the file is unaware that anything out of the ordinary happened. That's why Microsoft changed the default security setting to display a window asking permission similar to the one shown earlier.
However, users eventually get annoyed by pop-up warnings and wind up enabling macros without much thought about consequences. And, if users are really irked by pop-ups, they will figure out how to change the default setting, even posting information on the web for other disgruntled users -- all to the bad guys' delight.
Bad guys like macro-based malware because it is versatile and requires minimal effort on their part -- put together a spam run with a macro-based malware laden attachment and hit Send. If the unfortunate victim falls for the phish and the malware installs, the next step typically is the malware contacting the attackers. At which time, the bad actors either gain remote access and install more malware or make use of the information the macro-based malware harvested and relayed back to the attackers.
What's the answer?
Many of the earlier versions of macro-based malware are known to antimalware companies and are immediately quarantined. There's a "but" though. Bad guys have learned a thing or two in 10 years, and will try to keep ahead of the game by morphing anything that could be used as a defining signature by antimalware.
So, to be safe, most experts, including the antimalware companies, suggest vigilance. "As always we recommend users exercise caution when opening email attachments, even those from familiar or known senders," mentions Trend Micro's Salvador. "Ignore emails sent from unknown email addresses and especially avoid opening any attachments they may have. As an added measure, make sure to enable the macro security features in applications."
Also read
AV-Test proves antimalware apps can restore infected computers
Whitelisting has its place in your company's antimalware arsenal
Security and Privacy: New Challenges (ZDNet/TechRepublic special feature)
Note: TechRepublic and ZDNet are CBS Interactive properties.

