 Business 2 Community
Business 2 CommunityLet’s Get Serious About Personal Computer Security
Be vigilant. Be ready. Your personal computer security and online safety are on the line.

We are connected. But are we safe? How can we be vigilant about personal computer security and online safety for our many connected devices? This series examines facets of both computer and internet security, then offers some solutions and resources. The first in the series was about Phishing, the email scams abounding on the internet. This one is closer to home, looking at your desktop and laptop computers.
Extermination for Personal Computer Security
During the first half of the year I spent a lot of time building and maintaining websites. As small business owners — especially microenterprises — realize the power-punch a business website can deliver for them, it’s not surprising that the demand is there.
What is surprising is the number of small business owners, professionals and students who didn’t call me about creating or maintaining a website, but frantically got in touch because they needed extermination. You guessed it: the “bugs” and “fungi” they needed relief from had infested their computers or their websites, not their abodes.
They were concerned about personal computer security and keeping a clean machine.
My summer PC cleanup work prompted me to take a closer look at what my comrades in entrepreneurship should do and could do to better protect their technology assets — both their offline and online ones — to be prepared for potential disasters. And, should the situation warrant it, mitigate the associated costs. With that in mind, I wrote an ebook dealing about how to protect offline technology assets, specifically personal computers.
We Are Under Attack
Terminology
computer virus
malware
malvertising
spyware
adware
rogueware
scareware
ransomware
PuPs (potentially unwanted programs)
drive-by downloads
browser hijacker
The proliferation of adware, spyware, malware and every other kind of nasty compuerized equivalent of breaking-and-entering, espionage and all-aound bad manners is costly, time- consuming and emotionally draining.
Whether you encounter an in-your-face virus or are victimized in a stealthy manner — like the malware and fake tech support offer in the images below — you are the one left with the cost of cleaning it up. And you are the one who bears the brunt of the effect.
The emotional toll is often one of fear, leading you to ask questions such as:
How deep does this go?
Did I infect my family’s computers or friends or co-workers?
Is this my fault?
Did they steal anything?
Cyber-security analysts agree that if you are connected to the Internet, you are a potential target for malware infection. Ultimately, this means you are at risk on your personal devices as well as your online technology assets, i.e., business websites.
The need to be ever vigilant about personal computer security and online safety is increasing, not declining.
NastyWare

Popup Advertising Cartoon by Tom Fishburne, Marketoonist.com. Used with permission.
Cartoonist Tom Fishburne, who writes, speaks and draws about trends in advertising and marketing, highlights the ever-increasing trend in malvertising encountered on his Mac. He postulates that advertisers are in such a hot-and-heavy race to disrupt our attention spans that they either discount or ignore the potential for detrimental repercussions.
Says Fisburne:
Few marketing tactics are as hated as the pop-ad ad… Yet marketers continue to use them, aggressively (MacKeeper is a personal pet peeve)… I wonder if marketers are really factoring in the long-term costs of annoying their audience when they base decisions on short-term conversion factors alone. — Tom Fishburne, Popup Advertising
The really bad guys know about “advertising,” too. Hence, the moniker “malvertising.”
While legitimate advertisers’ sins may be of the disruptive ilk, nefarious rogue types are bent on bilking us for all we’re worth with their malicious disruptions. Instead of popping up and going away — or at least giving us the option to dismiss their annoying intrusiveness, they attempt to hold us hostage, going so far as to demand a ransom. Aptly dubbed ransomware, these activities define cyber-terrorism on a personal level.
Defense! Defense! Defense!
Been to a basketball game lately?
Those exuberant cheerleaders and enthusiastic fans cheering the team on to victory are shouting the mantra we need to adopt as our own: defense! defense! defense!
The coach has already hammered it home and it’s reinforced by echoes from the rafters: DEFENSE! We have to be our own coaches and take to heart the instructions, hear the faint(er) echoes, and follow the playbook.
First Line of Defense: Information
We all know the first line of defense in any situation comes from being armed with information (the playbook). For the sake of simplicity (and not overloading you with information), today just take a look at the items below and watch the short video. (You know, the coach makes the team watch recap videos, too!)
Second Line of Defense: Don’t Click
Contrary to popular belief, what we don’t know can hurt us. It behooves us to at least have an understanding of what the dangers are and what the preventive measures encompass. For example, the two images below are Microsoft Windows versions of a couple of nasties.
The one on the left is an example of malvertising: a fake offer for PC technical support. The popup claims to have found a number of errors on your computer and provide an 800 number you can call to get immediate assistance. Watch out for these and . . . Don’t click!
The one on the right is the same crap, different focus: It is a fake “speed optimizer” tool and looks legit because it name drops (Microsoft) and number drops (millions of users), but it is spyware or worse … Don’t click!
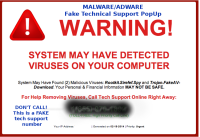
Personal computer safety: Watch out for malware, adware and fake technical support warning popups.

Fake Speed Optimizer Looks Legit (name and number dropping) but it’s Spyware or worse …
Third Line of Defense: Keep A Clean Machine
Just like locking your front door, bolting the back door, and battening down the windows are the first steps towards home defense, adopting a similar stance for online security and computer safety show your commitment to having a clean machine.
The best protection from interlopers is to limit their access and be prepared to oust them IF they gain access to your computers or electronic devices. A few simple steps will help in this regard:
Install both an anti-virus software program and an anti-malware (or anti-spyware) program on ALL computers.
If your programs of choice also have versions to protect your smartphone and other digital devices, install those, too.
Set these programs to auto-update.
Set them to run automatic scans.
Using a few simple tools coupled with due diligence goes a long way towards keeping you safe online and offline. BTW, the premium versions of tools that clearly add a convenience factor or extra protection is well worth the cost.
Respond to Threats: Get LOCAL Help
Sometimes, despite our best efforts and proper diligence with protecting our computers and digital devices, something slips through.
If you detect a threat you are not prepared to deal with by yourself, get local help. Why do I recommend local help? Because this will be someone you can see, touch and hold accountable.
When seeking local help first becomes a habit for you, you will not be inclined to click on some seemingly helpful (but fake) popup that digs you in deeper. And you will have an ally and expert nearby who will keep you on your toes concerning your safety throughout the year, provided you choose one who is worth his or her salt.
Thereafter, you can seek out a reputable online provider, if that makes sense for you.
This article was syndicated from Business 2 Community: Let’s Get Serious About Personal Computer Security
More Technology & Innovation articles from Business 2 Community:
