The leaked NSA report shows 2-factor authentication has a critical weakness: You

So you've created a strong password, kept an eye out for sketchy links, and enabled two-factor authentication — what could possibly go wrong?
Well, it turns out the answer is "you."
SEE ALSO: Here's what we know about alleged NSA leaker Reality Leigh Winner
As the leaked NSA report on Russian efforts to hack the computers of U.S. election officials before the 2016 presidential election demonstrates, we are all often our own biggest security weakness. The document, published by The Intercept, shows that hackers found a way around the protections offered by two-factor authentication that is striking in its simplicity: They asked the targets for their verification codes.
"If the victim had previously enabled two-factor authentication (2FA)," explains a slide detailing the Russian attack, "the actor-controlled website would further prompt the victim to provide their phone number and their legitimate Google verification code that was sent to their phone."
To translate, after tricking victims into entering their email and password into a fake Google site, the hackers found that some victims had 2FA set up on their accounts. This meant that even with the password, hackers were unable to gain access to the Gmail accounts in question — that is, unless they could get the verification codes as well.
So, again, they just straight up asked for them.
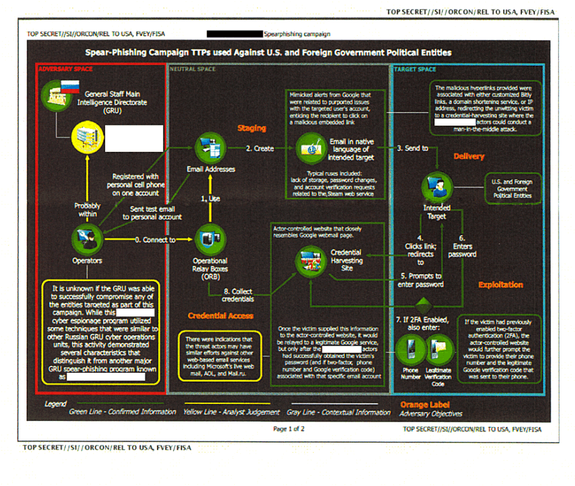
Image: nsa/the intercept
"Once the victim supplied this information to the actor-controlled website, it would be relayed to a legitimate Google service, but only after [redacted] actors had successfully obtained the victim's password (and if two-factor, phone number and Google verification code) associated with that specific email account."
Basically, the hackers were able to bypass the email security measures by requesting that the victims give them the keys to the digital castle.
Once access was gained to the accounts, which reportedly belonged to an electronic-voting vendor, the hackers would then email election officials from the hacked accounts and attempt to trick those same officials into opening script-laden Word docs that would compromise their computers.
It's an elaborate bit of spear phishing, and it reminds us that no matter what digital security practices we put in place, we can all still slip up.
In the face of everyday online threats, the best defense (other than setting up 2FA — which you should definitely still do) might be the simplest: exercise caution with every email you receive, and be paranoid as hell.
In the face of skilled Russian hackers? Well, that one's trickier, but maybe start with not handing over your email password, phone number, and 2FA verification code.
WATCH: Researchers are using sound to levitate objects, and it's changing the medical industry


