Nunavut government hit by ransomware attack
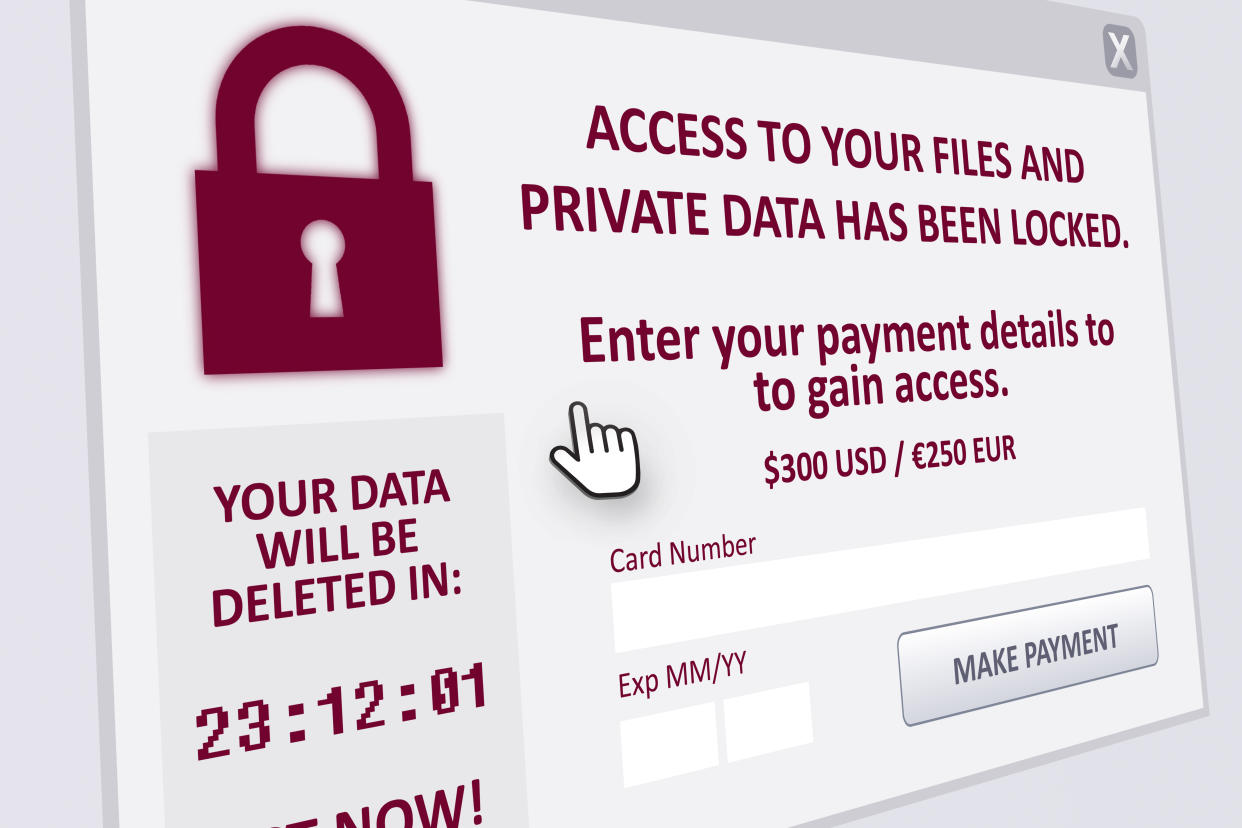
The government of Nunavut is the latest high profile administration to be the target of ransomware.
This brazen form of cybercrime is becoming increasingly common across North America. CNN reports that in the last year, there’s been more than 100 attacks on hospitals, police stations and government offices.
Ransomware is software written specifically to take control of, and take files from, a particular computing system. Once a system has been attacked, the only way to access the files on the system is to pay the cybercriminal a ransom — often in cryptocurrency — by a certain date to regain access to the affected files.
Last Saturday’s attack on the Nunavut government’s computer system encrypted all Microsoft Word documents and PDF files, making them inaccessible. Government employees, who were also locked out of work voice-mails and email accounts, are now using paperwork, telephones and faxes to communicate.
Since the government refused to pay a ransom, they must now individually check and reformat all 2,000 computers. Government officials told CBC they estimate the system will be back up and running in a few weeks.
How does ransomware work?
Robert Capps, vice president of market innovation for NuData Security, a Mastercard company, tells Yahoo Canada that ransomware attacks generally start with phishing.
“They’re sending out e-mails with attachments, to hundreds of thousands or millions of users at a time, and people are opening those attachments and it affects their computers,” he says.
There are also so-called drive-by downloads, where a pop-up ad will appear on a website, which has malicious software that executes and compromises the machines through a vulnerability in the computer’s web browser or operating system.
Capps says that there’s some evidence that cybercriminals behind ransomware attacks set their ransom based on the value of the organization or the individual.
“An average consumer might get a $200 ransom since they’re more likely to pay that,” he says. “If it’s $10,000, the average consumer will consider their computer trash and throw it away and buy a new one. But a few hundred dollars to get back baby pictures and tax records, that’s something someone might do.”
How can ransomware be avoided?
The best way to protect yourself from ransomware is to be wary of e-mails with attachments, or avoid clicking links in emails that are unfamiliar or unexpected.
It’s also important to have the latest software updates available for your computer, as well as the latest security software, like anti-malware. That should cover the majority of exposures to most organizations, says Capps, but doesn’t totally exclude them from being vulnerable.
Targeted attacks against large corporations are called spear phishing, where an attacker will send crafted email to specific people, purporting to be someone within the organization with authority. It then asks the user to download a file or run an attachment.
“In those cases some of the applications don’t even have to look for a vulnerability,” he says. “The user is actually executing them and running them. It’s more of human malice that needs to be dealt with.”
Capps says it’s important for computer users to know that downloading files, even from a known contact, can be risky. He suggests contacting the person who sent the email by phone to confirm it is a legitimate source, before downloading anything.
“It’s key to understand that consumers hold a lot of power here and not falling victim to these crimes in a large part is within their power,” says Capps. “Being safe around emails, making sure software and security software is up to date, that’s going to get them a long way. Being aware and diligent around e-mail access is still really important.”

