Unpatchable AMD Chip Flaw Unlocks Paid Tesla Feature Upgrades
Teslas are among the most popular electric cars on the market, which makes them an easy target for hackers. Now, a team of security researchers from TU Berlin has found a way to exploit the MCU found in modern Tesla vehicles to unlock paid features and more. To execute the attack, the researchers exploited a known flaw in AMD's processor that controls Tesla's MCU.
In Tesla parlance, MCU stands for Media Control Unit, and it controls the touch screen, navigation, and entertainment systems. MCU0/1 refers to the first generation (Nvidia Tegra-based), while MCU2 is the second generation (Intel Atom). MCU-Z refers to the third generation based on a custom AMD Ryzen SoC. MCU-Z is the subject of the researchers' attention.
According to the researchers, they used a voltage fault injection attack (a certain class of attacks) against the MCU-Z. This class of attacks is also known as 'voltage glitching,' and is a known attack vector for Zen 2- and Zen 3-based processors; it also affects the Ryzen SoC used in Tesla's MCU-Z. Utilizing multiple connections to the power supply, BIOS SPI chip, and SVI2 bus, the researchers performed a voltage fault injection attack on the MCU-Z's Platform Security Processor. With a successful attack, objects stored in the Trusted Platform Module (TPM) can be decrypted.
"Our gained root permissions enable arbitrary changes to Linux that survive reboots and update," the researchers explain. "They allow an attacker to decrypt the encrypted NVMe storage and access private user data such as the phonebook, calendar entries, etc."
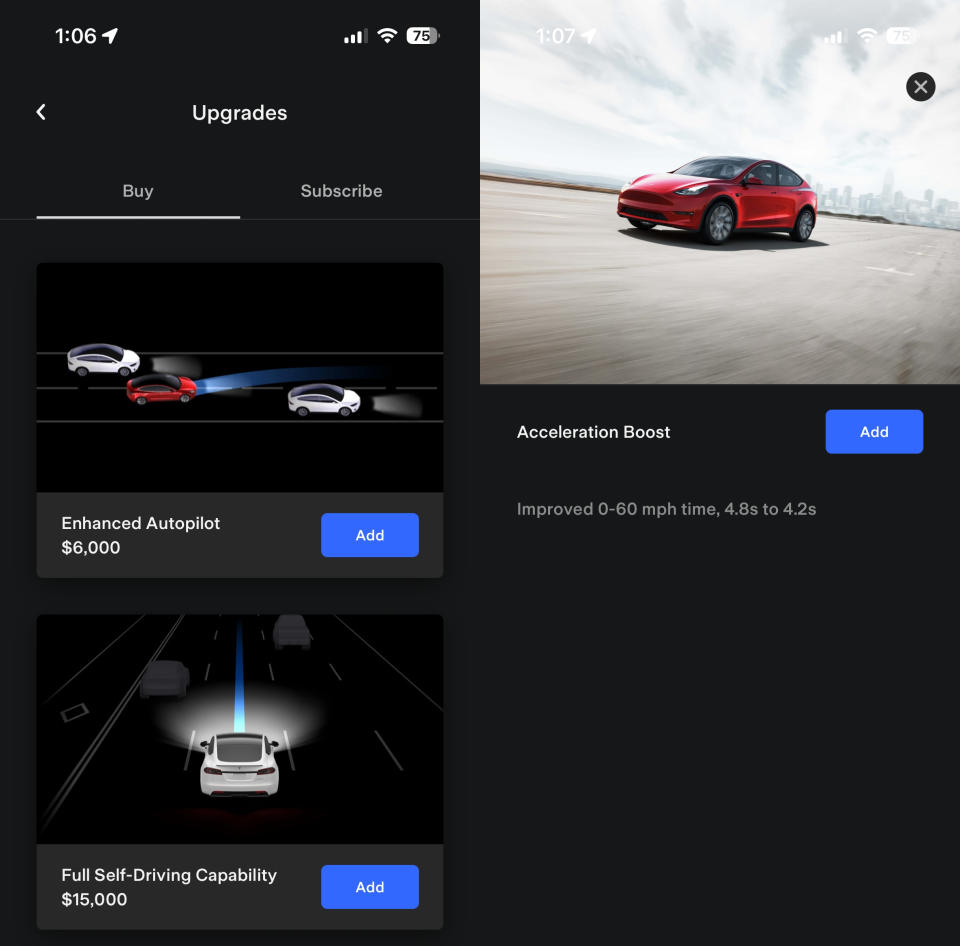
Unsurprisingly, this exploit can provide access to various Tesla subsystems and even optional content usually locked behind a paywall. Depending on the Tesla vehicle in question, some features are software locked and can be purchased and enabled after delivery using the vehicle's touch screen system or via the Tesla app.
"Hacking the embedded car computer could allow users to unlock these features without paying," the TU Berlin researchers add. For example, 2021 Model 3 SR+ vehicles can enable the Cold Weather Feature (heated steering wheel, heated rear seats) for an extra $300. This feature unlock is confirmed to work with the exploit.
Tesla Model Y Long Range owners can also pay $2,000 for Acceleration Boost, which decreases the 0-60 times of the vehicle from 4.8 seconds to just 4.2 seconds. Pricier options include Enhanced Autopilot, which costs $6,000, and Full Self-Driving, priced at an eye-searing $15,000. In an email to Tom's Hardware, one of the researchers clarified that not all Tesla software upgrades are accessible, so it remains to be seen if those premium options will also be ripe for picking.
What's interesting to note about this flaw is that it is "unpatchable," meaning that Tesla has no known mitigation solutions to counter it. Another consequence is that the exploit can "extract an otherwise vehicle-unique hardware-bound RSA key used to authenticate and authorize a car in Tesla's internal service network."
What does that mean in English? Suppose a Tesla vehicle was totaled in a severe crash or flooded. It would be flagged in Tesla's system as such and would not be eligible for access to Tesla services, like the Supercharging network. However, this could allow a salvage-titled Tesla to access the Supercharging network, much to the chagrin of Tesla, which wouldn't want to risk damage to its charging hardware with a busted car.
The TU Berlin team (consisting of PhD students Christian Werling, Niclas Kühnapfel, and Hans Niklas Jacob, along with security researcher Oleg Drokin) will present their findings next week (August 9) at the Blackhat conference in Las Vegas, where we hope to hear more about all the feature upgrades that are accessible. Werling and Jacob were also on the team responsible for discovering the original faulTPM voltage fault injection attack.
**Updated August 3 @ 4:51 PM ET**
The article was updated with clarification from the TU Berlin researchers on which feature upgrades are confirmed to work with the exploit.

