100 Days Post-Roe: This FemTech Lawyer Broke Down Everything You Need To Know About Data Privacy And Period Tracking Apps To Protect Yourself Online
This past Sunday, October 2 marked 100 days since the Supreme Court overturned Roe v. Wade, leaving the right to abortion federally unprotected. In that time, 13 states have criminalized abortion, while others have severely restricted its access. Retail chains have limited the purchase of Plan B pills due a surge in demand. And Meta made headlines for turning over private data to law enforcement officers investigating a 17-year-old girl in Nebraska for allegedly using abortion pills.

Consequently, states with abortion access have subsequently received an influx of patients. In August, clinics in Illinois reported that 86% of patients came from out of state, with the increase in patients causing three-week wait periods.
As people struggle to protect themselves in post-Roe America, it's become abundantly clear that data privacy is a major concern. Even before the overturn, movements (and tweets) called for the deletion of period tracking apps in fear that users' reproductive health data could be used against them. But seeing as to how detectives in the Nebraska case "noticed" the teen's uses of Facebook Messenger (and subsequently subpoenaed Meta for her private messages), are period tracking apps really what we should be afraid of?
If you are in the United States and you are using a period tracking app, today is good day to delete it before you create a trove of data that will be used to prosecute you if you ever choose to have an abortion.https://t.co/7L7LaQizgx
To help break down what you actually need to know when it comes to data privacy and abortion, BuzzFeed spoke with Bethany Corbin, JD, LLM, CIPP/US, CHC, CHPC. If you're drowning in her alphabet soup of degrees, here's the bottom line: Bethany is a healthcare innovation and femtech lawyer, and she outlined six tips on how you can protect your data privacy post-Roe.

FYI: Femtech is a portmanteau of "female health technology," such as period tracking apps. The term was coined in 2016 by Danish entrepreneur Ida Tin, the founder of the period- and fertility-tracking app Clue. According to McKinsey, femtech has since "grown to encompass a range of technology-enabled, consumer-centric products and solutions," with estimates of its current market size ranging from $500 million to $1 billion.
Now, if you're confused as to why data privacy, overall, poses a bigger risk than period tracking apps when it comes to the criminalization of abortions, look at it this way: Health data could show that you were, at one point, pregnant, and then you weren't. But that's circumstantial at best. Maybe you had a miscarriage. On the other hand, if you straight-up text your mom that you want to have an abortion and then order abortion pills — well, prosecutors have a much stronger case against you based on your private messages and internet search history.

In fact, the Nebraska case isn’t the first time something like this has happened (though it is since Roe has been overturned). Back in 2017, Mississippi police used a woman’s phone data and search history for abortion pills to charge her with second-degree murder.
Similarly, it's less likely that law enforcement officers would know to subpoena data from your period tracking app. "They have to have reasonable suspicion in order to issue that subpoena or court order to get your data," Bethany explained. "Where are they going to find that? It's likely going to be more mainstream channels, like social media and Google searches."
Though some companies have announced that they will not turn over data for abortion-related cases, it's unlikely that they'll always know what the case involves unless it's explicitly stated in the subpoena. Case in point: After the charges in the Nebraska case came to light, Meta issued a statement revealing that "the warrants did not mention abortion at all."

So then why the heat on period tracking apps? Well, probably because they’re the ones openly collecting reproductive health data. If Clue or Eve were subpoenaed for user data, it’s more likely to be for a case involving reproductive health than if a big tech company were subpoenaed.
To give you a better idea, between Jan.–June 2021 in the US, Google received more than 50,907 government requests for user data and produced data for 82% of requests, while Meta received more than 63,657 government requests for user data and produced data for 89% of requests.
Before we dive into how to protect yourself online, let's talk data practices 101, as in what most companies do with your data. Think of data as currency in surveillance capitalism. In order to use an app, you need to make an account, ultimately compensating with some of your data. "That's how they make their money," Bethany said. "They collect more data than needed to make the app function, bundle it together, and sell it to a data broker who could then sell that data to anyone — to you, me, law enforcement — who'd otherwise need a subpoena to get it from the company itself."

For certain apps, the service is the data, like your internet searches on Chrome or your geolocation on Uber. "Truthfully, we're just in an environment in which that data can be used, sold, and disclosed, without any further consumer say," Bethany commented. "You don't have a meaningful way to negotiate that data or to negotiate how it's going to be used or to opt in."
While selling user data as a major revenue stream is common, the overturn of Roe has sparked massive public scrutiny of data practices, especially in femtech. So here are six ways you can protect your data privacy as it relates to reproductive health in post-Roe America (and no, they don't necessitate deleting your period tracking app):
1.Read the disclosure section of privacy policies, as well as updates. Since period tracking apps collect health data, there's a misconception that HIPAA protects users. "The thing is, HIPAA doesn't apply to the data," Bethany revealed. "It applies to the entity type. You could give the exact same data to your healthcare provider and an app, and it's protected while in the provider's possession and not while in the app." So because femtech apps aren't created by covered entities, they're treated as tech solutions rather than healthcare. Many apps fall into a regulation gap as a result, subject only to state privacy laws and the FTC, which prohibits unfairness or deception toward consumers. Basically, companies can do whatever with your data so long as they're upfront about it.

Essentially, the FTC requires companies to disclose how they collect and use your data in transparent, accurate privacy policies. So if a company wants to sell your data to a third party, they can so long as it's clearly stated in their privacy policy. What that third party then does with your data is irrelevant — it's on you to read their privacy policy. Plus, privacy policies are not absolute. Companies can and must update them whenever they change their data practices, so read all updates too. By continuing to use the app, you're consenting to the updated privacy policy.
For a real-life example: In 2019, the FTC filed a complaint against Flo for misleading users after the Wall Street Journal reported that the period tracking app had been sharing users' data with marketing and analytics firms, including Facebook and Google, despite Flo's privacy policy stating it wouldn't send such information to third parties. "Flo could have legally sold data to Facebook if it had just said that in its privacy policy. It was the fact that it said it was not dealing with that express action that got it in trouble with the FTC," Bethany explained.
Beyond femtech, HIPAA-covered entities — like your healthcare provider with whom you share your medical history — can still be subpoenaed. "A lot of people don't realize there's a permissible disclosure in HIPAA for law enforcement and court orders. So, technically, if your provider got a subpoena to turn over your data, they could do it lawfully," she added.
2.Use encrypted messaging. Generally speaking, encryption encodes information to prevent anyone other than the sender and recipient from seeing it. So if a company received a subpoena for messages that were encrypted, it wouldn't actually have access to that data, let alone be able to provide it to law enforcement.
This is, in part, why activists — from Black Lives Matter activists to sex worker activists — have been calling for encrypted data and messaging for years.
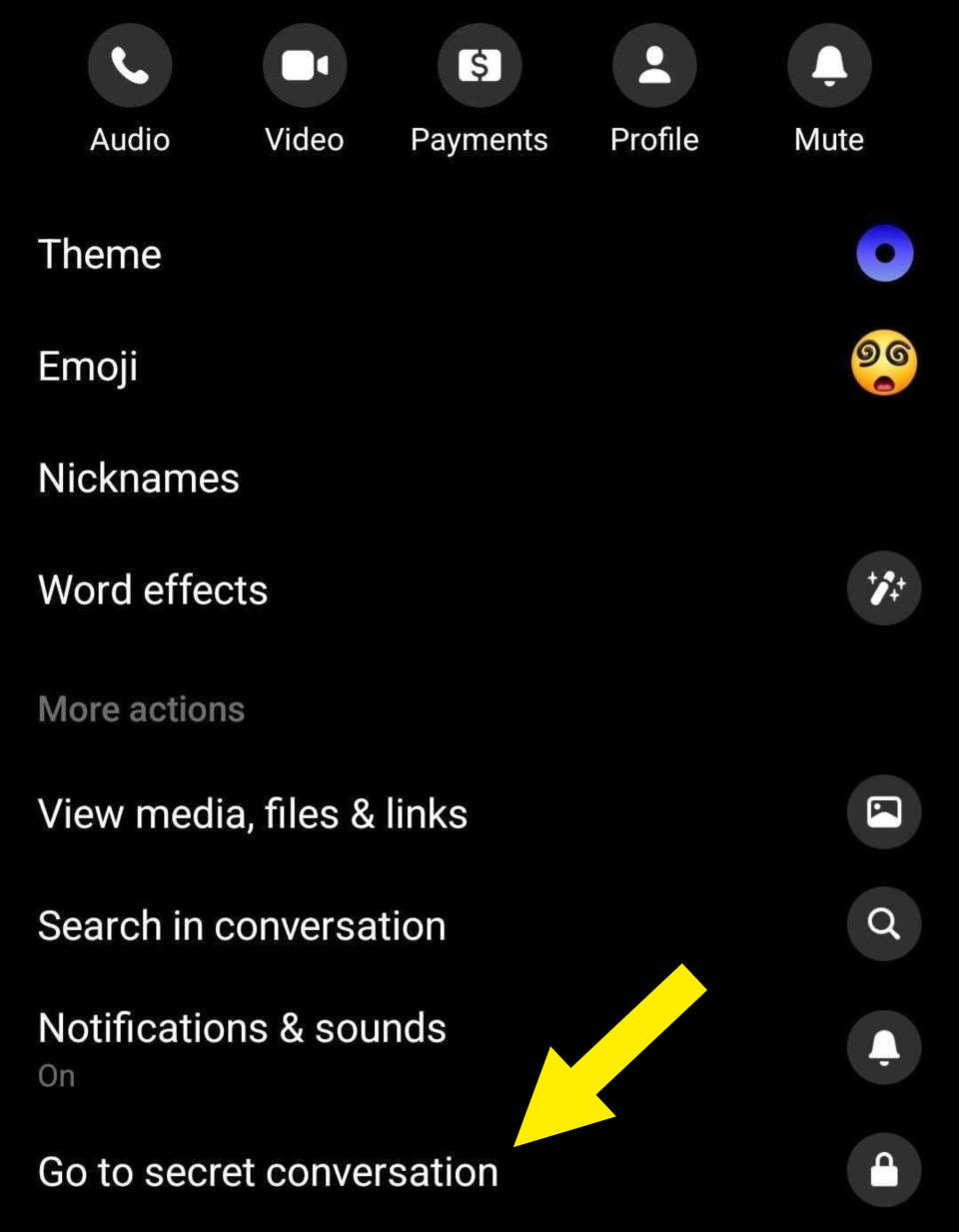
On that note, in recent years, Facebook Messenger has begun offering an encrypted messaging feature that users can opt in to for individual chats. You can activate encrypted messaging per chat by selecting the "i" icon in the top-right corner, and then choosing, "Go to secret conversation" under the "More actions" section.
3.Understand that any "anonymized" data can be reidentified when using new, well-intentioned features. For example, Flo's Anonymous Mode "deidentifies data…by removing personal email, name and technical identifiers." However, anonymized data can often easily be linked back to you by matching it with another set of data (usually that's publicly available), thus revealing whom the data belongs to.

"In today's world, there's very little that cannot be reidentified if somebody tries hard enough and has the right technology. It might be anonymous until it gets into the wrong hands," Bethany cautioned. In fact, a 2019 study found that 99.98% of Americans would be correctly re-identified in any dataset using 15 demographic attributes (such as age, zip code, birthdate, marital status, etc.).
If you’re curious about how data can be deidentified and reidentified, consider the data that an app could collect about you: name, birthdate, address, email, phone number, geolocation, gender, etc. Obviously, data like your name or address could directly identify you, whereas data like your zip code or gender could indirectly identify you. By scrubbing certain identifiers, data can be anonymized, and indirect identifiers — though ambiguous separately — can reidentify users when properly combined.
4.Keep in mind that data can be manually accessed. Let's be real — we live in a near-entirely digitized world, so you might be thinking that the best way to track your cycle is to use an app that locally stores your data (as in, on your phone vs. in the cloud) or to jot it down in your Notes app. Unfortunately, that's still not foolproof. Law enforcement can just as easily subpoena your device and access the data directly.
"Unless you’ve gone through and physically deleted all of the data off your phone — which, to be honest, probably also lives in some type of a backup online — law enforcement is going to get access to that data," Bethany said.
5.Look into where the company behind your app physically stores data, as the state's legal structure will impact how your data could be turned over to law enforcement. "I've seen some companies thinking through whether or not they should move things — like their hard drives, data storage facilities, etc. — out of states that are banning abortion," Bethany added, as law enforcement can more easily obtain data stored in states banning abortion than in states defending it.
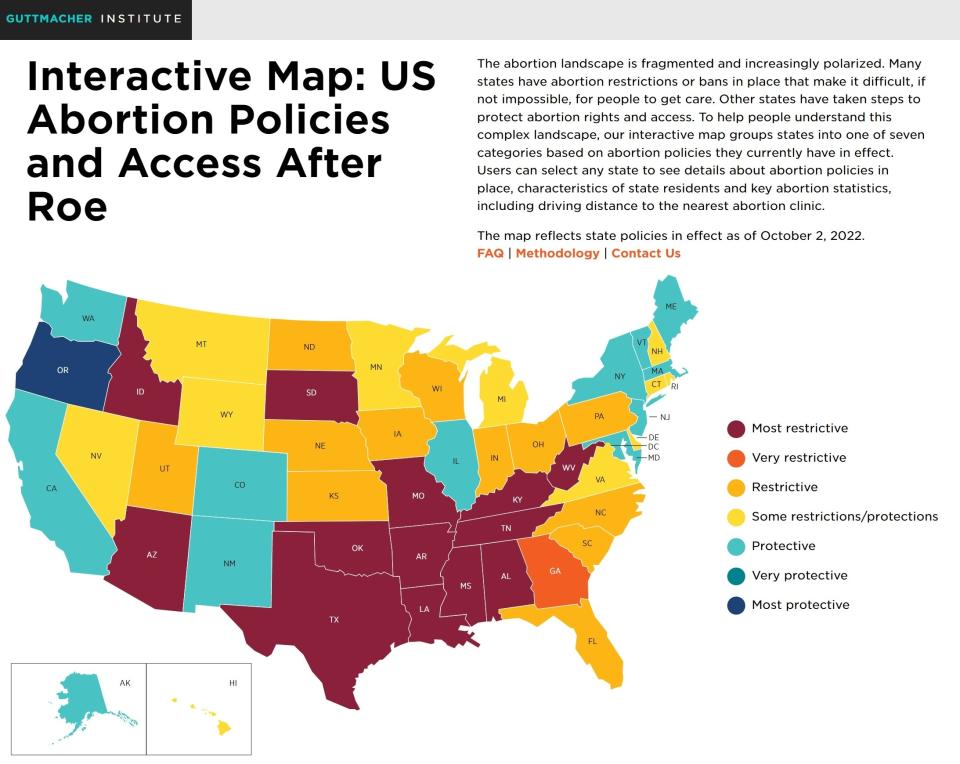
For instance, New York has enacted laws to protect patients and healthcare providers from states "looking to impose their policies" and "punish providers beyond their borders." This involves preventing law enforcement from cooperating with out-of-state agencies, i.e., enforcing out-of-state subpoenas or court orders. Connecticut has similarly enacted "safe harbor" laws, while California, Oregon, and Washington have banded together to launch a "multi-state commitment” defending reproductive healthcare access and protecting patients and healthcare providers alike from punitive states.
These protective laws are in stark contrast to "bounty hunter laws," such as Texas’s Senate Bill 8 (SB8 for short). Passed in 2021, it incentivizes citizens to sue anyone who’s helped someone have an abortion by rewarding them a cash “bounty” if they win. SB8 has inspired similar laws in Idaho and Oklahoma.
You can find state laws around abortion via the Guttmacher Institute’s State Legislation Tracker here and their interactive map of US abortion policies here.
6.Recognize that data security is not infallible. Or, as Bethany put it, "It's not a matter of if — it's a matter of when — that company is going to experience a data breach or a data leak." Just like you've received regretful emails from your email provider to change your password because they've been hacked, so, too, can your period tracking app or messaging app be hacked. Unfortunately, data leaked through hacks could be used to extort not only the company responsible for it but also the individual user, especially in states that ban abortion.
Pre-Roe, a 2019 report by Trustwave found that a healthcare data record is worth up to $250 on the black market, while a payment card, the second most highly valued record, is worth $5.40.
"It's because there's so much information in there that somebody can go and use to steal your identity. You can't change your health data like you can change your credit card number," Bethany explained. And with states banning abortion, the value of health data has skyrocketed.
At the end of the day, Bethany's best advice — which she acknowledged "nobody really wants to hear" — is to not put anything online (or in an app) that you're not comfortable with being made public. As long as your data gives inference to the fact that you were pregnant and then not pregnant (and didn't give birth, of course), law enforcement could have reasonable suspicion to investigate. However, it's just as important that we don't rage against or abandon femtech either.
If you do choose to delete your period tracking app, confirm that deleting the app automatically deletes your data. Sometimes, companies will only delete your data upon request, if at all.
While big tech needs to be held accountable, it's also true that women's healthcare has historically been neglected, and femtech has the potential to revolutionize it, from accessibility to medical research. And therein lies the irony that femtech — intended to improve women’s healthcare — bears the brunt of the post-Roe data privacy scrutiny rather than tech and data regulations as a whole.

In a fight for the right to bodily autonomy — in a society that simultaneously denies reproductive healthcare, refuses reproductive health education, stigmatizes reproductive health resources, and places the onus of bodily regulation and pregnancy entirely on those with a uterus — technology that enables us to privately educate ourselves and autonomously manage our health is villainized.
And while limiting the data you enter into a period tracking app may provide a greater chance of privacy, the apps naturally work best and make the most accurate predictions when you provide more information.

